In this articles, I’ll tell you about DOS and DDoS. What it is basically a cyber-attack on a specific server or a network with the intended purpose of disrupting that network or server’s normal operation. The DDoS attack does this by flooding the targeted network or server with a constant flood of traffic such as fraudulent requests which overwhelms the system causing a disruption or denial of service to legitimate traffic.
WHAT IS DOS AND DDoS ATTACK?
What is a DOS attack?
DOS attack stands for denial of service attack which means a single attacker attacking a single target this means that one computer and one internet connection is used to flood the server with packets. The attacker sends a large number of legitimate looking to the server in a way that the server cannot really distinguish between valid and non-valid requests. It will overwhelm the system to a point that the server cannot handle the capacity anymore.
The purpose if such denial of service attack is to overload the targeted server’s bandwidth and other computing resources this will make the server inaccessible to others.
What is a DDoS attack?
DDoS attack stands for Distributed Denial of Service Attack. In most cases, the DDoS attack is similar to DOS attack but the result is much different instead of one computer and one internet connection in normal DOS attack the DDoS attack utilizes many computers and connections. The computer behind such an attack are often distributed around the whole world and will be part of what is known as abundant.
HOW DDoS ATTACK WORKS?
The first step in launching a DDoS attack is to recruit an army of bots. In order to turn a computer into a bot, the attacker develops a specialized malware which spreads to as many vulnerable computers as possible.
Malware can spread via compromised websites, email attachment or through an organizations network. Users who are tricked into running such a malware will intentionally turn that computer in a bot and provide access points to the attackers to their computers.
Once the computer turns into a bot it connects to the attacker’s command and control server and begins to accept orders from the centralized machines. The orders from the command and control server include the direction for launching an attack from bots malware to a particular target and the selected attacking method. The army of bots is known as a botnet.

Let’s take an example we have a web server and this web server belonging to a company that sells their product over the internet. Let suppose we have a couple of customers as you can see in the figure with their computers that are browsing the company’s website looking at the company’s products or services.
Now just suppose that someone just wanted to do an attack on this company’s web server for whatever reason for example attacker don’t like the company or the owners of the company.
So what will attacker do he will use his computer and program to attack this server and flood it with fraudulent data traffic to try and disrupt its service. Now, this is not a DDoS attack this is just called a DOS attack which stands for denial of service because a DOS attack is an attack that’s just coming from one source.
Normally a network or server is able to handle an attack from a single source because it’s easier to pinpoint the server can just simply close the connection where the attack is coming from so, that’s not really a problem, however, the problem is that what if an attack comes from multiple sources simultaneously and that is what a DDoS is.
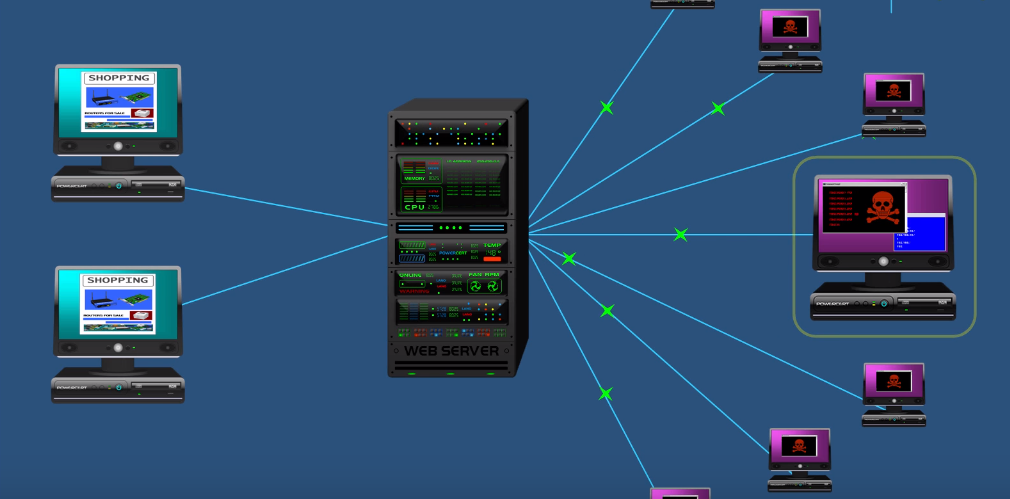
DDoS is an attack from multiple sources all at once. The computer which is highlighted is the ringleader can communicate with other computers around the world and coordinate an attack on this server so instead of an attack coming from a single source the server now has to deal with an attack from multiple sources. when this happens it will overwhelm the server and it will eat up the server’s system resources such as the CPU and memory and it will also eat up network bandwidth. So, as a result, these legitimate computers over here are going to be denied service because the server is too preoccupied with dealing with a DDoS attack.
So, the webpage is that these computers want to access or either not going to load or they are going to be very slow in loading and they’ll get that familiar spinning wheel of lag on their screens.
So, the question is how the does the attacker get involve the other computers to get involved in a DDoS attack and the simple answer is by using the malicious software. The attacker will develop a malware program and distribute it over the internet and put it on things like websites and email attachments.
If a vulnerable computer goes to these infected websites or opens these infected email attachments the malware will be installed on their computer without the owner even knowing that their computer has been infected. Their computer has been recruited in an army of other infected computers to perform a DDoS attack. This army of infected computers is what’s called a botnet. The botnet is an army of infected commuters to do a DDoS attack.
The botnet is not just limited to a few computers, the botnet could be hundreds or even thousands of computers that are scattered all over the world. So, this botnet can be controlled like an army waiting to receive instructions from the attacker who is now the like a centralized command and control center for the botnet and then the attacker can send out commands to all these computers and tell them to attack at a certain date and time and then once set time is reached the attack begins. The DDoS attack can last for hours or even days it just depends on the attackers intent.

So, another question is why do people do DDoS attacks? DDoS attacks can happen for several different reasons, for example, it could be for financial reasons and the attacker is ddossing a competitor in the marketplace or attacker is just doing it for fun.
What is the main difference between DOS and DDoS Attack?
The main difference between DOS and DDoS attack is that there is only one attacker in DOS attack but in a DDoS attack the target server will be overloaded by hundreds or even thousands of requests, so, therefore it is much harder for the server to withstand a DDoS attack than a DOS incursion.
How to prevent a DDoS Attack?
The DDoS attack comes in many different forms and one of them is called Trojan. The attackers usually send the link with children and if the victim opens the link the attacker can do whatever he wants with the computer so the simplest way to avoid a DDoS attack is making sure not open anything that you are not known of. You can also get a professional company to help you mitigate the attacks. If you are serving your own data then make sure all your routers drop junk packets block ICMP when you don’t need it and set up a strong firewall.
How companies prevent a DDoS attack?
Large companies leave a significantly larger capacity than they need to for a DDoS attack if the attacker is unable to take over enough traffic of the site the attack is generally ineffective. Some Companies have tools which monitor net flow data from routers to determine a baseline for traffic. If they detect any traffic that steps out of the zone the DDoS mitigation tools can attract the traffic and filter it out. Many large companies often implement either a DNS based redirect service or a BGP based services to protect them from attack.










